Difference between cyber security pentesting and red team activity
Overview of Cyber Security Pentesting and Red Team Activity
Definition of Cyber Security Pentesting
Cyber Security Pentesting, commonly referred to as penetration testing, is a proactive approach towards identifying vulnerabilities within a system or network before malicious entities exploit them. Think of it as a controlled simulation where skilled professionals, known as penetration testers, attempt to breach a client’s security measures. The aim is to uncover weaknesses, misconfigurations, or loopholes to strengthen the security posture of an organization.
- Key Aspects of Pentesting:
- Simulated Attacks: Pentesters mimic real-world attack scenarios to gauge the effectiveness of security measures.
- Vulnerability Assessment: Analyzing the infrastructure to identify unpatched software, open ports, and weak protocols.
- Reporting: After tests, comprehensive reports detailing the findings, potential impacts, and remediation steps are provided to stakeholders.
For example, a financial institution might hire pentesters to simulate a cyber attack on their online banking system, discovering vulnerabilities that would permit unauthorized access.

Definition of Red Team Activity
In contrast to penetration testing, Red Team Activity embodies a more holistic approach to cyber defense. Red Teams consist of skilled attackers who assess not only technology but also processes and people within an organization. Their role is to adopt the mindset of potential adversaries, aiming to find gaps in security measures through more extensive and unpredictable means.
- Key Features of Red Team Activity:
- Realistic Threat Simulation: Red Teams mimic authentic cyber-attack techniques, often without the organization’s affiliates being aware.
- Holistic Approach: This includes evaluating physical security, personnel training, and incident response capabilities alongside digital infrastructure.
- Continuous Improvement: Insights gained from Red Team exercises are utilized to improve defenses, workflows, and employee training programs.
An example of a Red Team Activity could involve a team running a social engineering campaign by attempting to gain physical access to a corporate facility, testing not only technical defenses but also employee awareness and adherence to security protocols. Both Cyber Security Pentesting and Red Team Activity are critical components of a robust security strategy, each targeting different dimensions of security and vulnerabilities, ultimately working towards the common objective of fortifying defenses against cyber threats.

Objectives of Cyber Security Pentesting and Red Team Activity
Goals of Cyber Security Pentesting
The primary goal of Cyber Security Pentesting is straightforward: assess the security of an organization’s infrastructure to safeguard sensitive data and resources. By simulating attacks, pentesters aim to pinpoint vulnerabilities that could lead to a disastrous breach.
- Key Goals of Pentesting Include:
- Vulnerability Identification: Recognizing weaknesses within applications, networks, and systems before cybercriminals discover them.
- Mitigation Strategies: Providing actionable insights on how to address and fix the identified vulnerabilities, ensuring a stronger defense.
- Compliance Requirements: Meeting industry regulations and standards by demonstrating thorough testing and risk management practices.
For instance, a healthcare provider may engage pentesters to evaluate their patient data management systems. This not only protects sensitive information but also adheres to regulations like HIPAA.
Goals of Red Team Activity
Red Team Activity expands on the objectives of pentesting, focusing on simulating advanced persistent threats that reflect what real attackers might do. The goal is to assess not only technological defenses but also organizational preparedness.
- Key Goals of Red Team Activity Include:
- Realistic Threat Exploration: Uncovering how an organization reacts to varied attack vectors, including social engineering and insider threats.
- Holistic Security Assessment: Evaluating technical, physical, and human resource vulnerabilities to provide a 360-degree view of security posture.
- Enhancing Incident Response: Testing and enhancing the effectiveness of the incident response plan, creating a stronger equilibrium between technology and personnel resilience.
For example, during a Red Team engagement, a restaurant’s staff might be targeted through phishing emails designed to gain access to sensitive customer data. By investigating this scenario, the organization learns not just about their technological flaws, but also about the gaps in employee training regarding phishing threats. In summary, while Cyber Security Pentesting provides a focused examination of specific vulnerabilities, Red Team Activity offers a broader perspective, assessing an organization’s overall defense and preparedness against real-world cyber threats. Integrating both objectives creates a fortified security landscape, empowering organizations to thrive in an increasingly complex digital environment.

Methodologies in Cyber Security Pentesting and Red Team Activity
Techniques Used in Cyber Security Pentesting
Cyber Security Pentesting employs a range of techniques designed to mimic potential attackers and evaluate the security landscape. These techniques focus primarily on uncovering vulnerabilities to guide remediation efforts effectively.
- Common Pentesting Techniques:
- Reconnaissance: Gathering information about the target system or network, which is crucial in formulating an attack plan. This can involve using tools like Nmap to scan for open ports or services.
- Exploitation: Actively testing the vulnerabilities identified during initial assessments. This could involve using known exploit frameworks such as Metasploit to gain access to systems.
- Post-Exploitation: Once access has been gained, pentesters explore what an attacker could do afterward, such as data exfiltration or lateral movement within a network.
For example, during a pentest on a cloud-based application, a tester might start by identifying all endpoints before attempting SQL injection attacks to access sensitive user data.
Approaches in Red Team Activity
The methodologies in Red Team Activity differ significantly, highlighting a more comprehensive and adaptive strategy. Here, the focus shifts from strict penetration testing to simulating real-world adversaries, exploring a spectrum of tactics, techniques, and procedures (TTPs).
- Key Approaches in Red Team Activity:
- Adversarial Simulation: Red Teams enact attacks across different vectors, including digital, physical, and social engineering, creating realistic multilingual schematics of how potential threats might operate.
- Plausible Deniability: Often acting covertly, Red Teams can simulate scenarios that may go undetected, allowing organizations to gauge their response capabilities without prior knowledge of the exercise.
- Scenario-Based Testing: Engaging in role-playing exercises to illustrate the decisions an attacker might make in various situations. For instance, a Red Team might exploit a vulnerability to socially engineer an employee into compromising sensitive information.
Imagine a scenario where a Red Team deploys a phishing campaign to test employees’ awareness and responses. This not only reveals technical flaws but also indicates how well-trained the staff is in recognizing threats. In summary, while Cyber Security Pentesting relies on clear-cut methodologies aimed at identifying specific vulnerabilities, Red Team Activity embraces a broader strategic approach that mimics genuine threats, thereby enhancing organizational resilience. These methodologies play complementary roles, ensuring that both technical and human factors are understood and fortified against cyber threats.
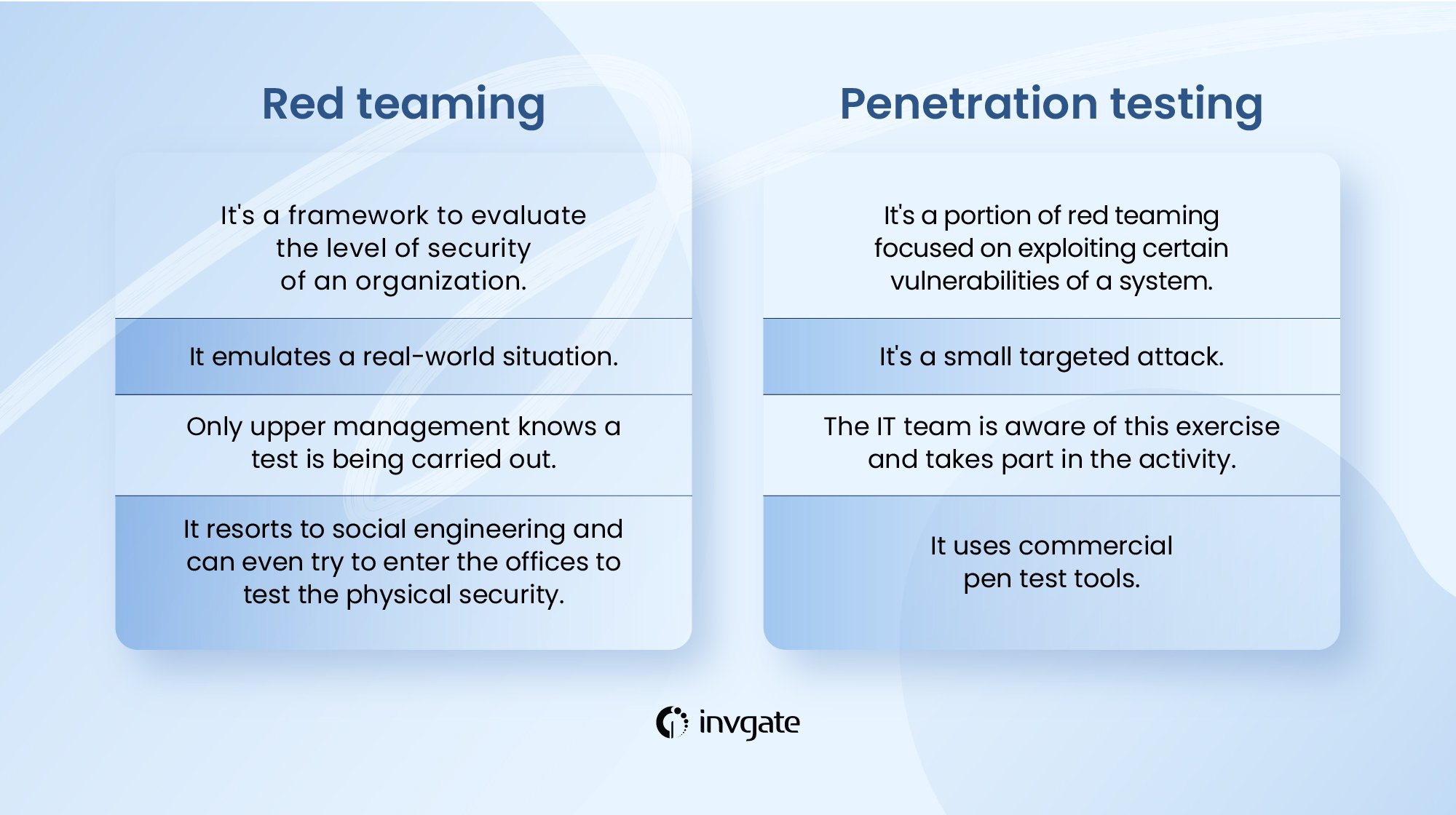
Differences Between Cyber Security Pentesting and Red Team Activity
Focus Areas in Pentesting vs. Red Team Activity
When it comes to Cyber Security Pentesting and Red Team Activity, the focus areas distinctly set these two practices apart. Understanding their differences helps organizations choose the right approach to fortify their defenses.
- Cyber Security Pentesting Focus:
- Specific Vulnerabilities: Pentesting zeroes in on particular systems, applications, or network segments to identify known vulnerabilities.
- Technical Evaluation: This method emphasizes verifying technical controls, configurations, and specific attack vectors.
- Actionable Findings: The end goal is to produce a report detailing vulnerabilities and remediation strategies tailored to the tested environment.
For instance, a company may hire pentesters to evaluate the security of their internal web application. Their findings will be concentrated explicitly on that application, detailing any flaws found and recommendations for improvement.
- Red Team Activity Focus:
- Holistic Threat Simulation: Red Team efforts look at broader attack surfaces, including human behaviors and organizational processes.
- Adaptive Strategies: These teams often adopt an array of techniques, mimicking actual adversaries and adjusting strategies based on real-time observations.
- Continuous Improvement: The focus extends beyond immediate vulnerabilities to assess how well the organization can detect, respond to, and recover from various types of attacks.
For example, during a Red Team engagement, attackers might deploy social engineering tactics on employees while simultaneously probing technical defenses, evaluating both human and machine responses together.
Scope of Testing in Pentesting and Red Team Activity
The scope of testing further delineates these two methodologies and defines their operational boundaries.
- Pentesting Scope:
- Defined Parameters: Pentests generally have a clear set of boundaries established upfront, determining the specific systems and types of tests to be conducted.
- Time-Bound Testing: Often conducted within a set timeframe, pentests are typically repeatable engagements focusing explicitly on technical vulnerabilities.
- Red Team Activity Scope:
- Fluid and Iterative: Red Team tests are more fluid, with teams able to adapt and change tactics dynamically based on the organization’s defenses.
- Comprehensive Testing: The scope can include physical security, human factors, and even reactive measures, ensuring a well-rounded assessment of the overall security posture.
For instance, in a Red Team scenario, the scope may evolve as attackers discover vulnerabilities, prompting a deeper exploration of additional defenses within the organization. In essence, while Cyber Security Pentesting and Red Team Activity may share common goals of identifying vulnerabilities and enhancing security, their focus areas and scopes differ significantly. Understanding these distinctions allows organizations to better allocate resources and choose an optimal security strategy tailored to their specific needs. This holistic view ensures a tighter security net against ever-evolving cyber threats.
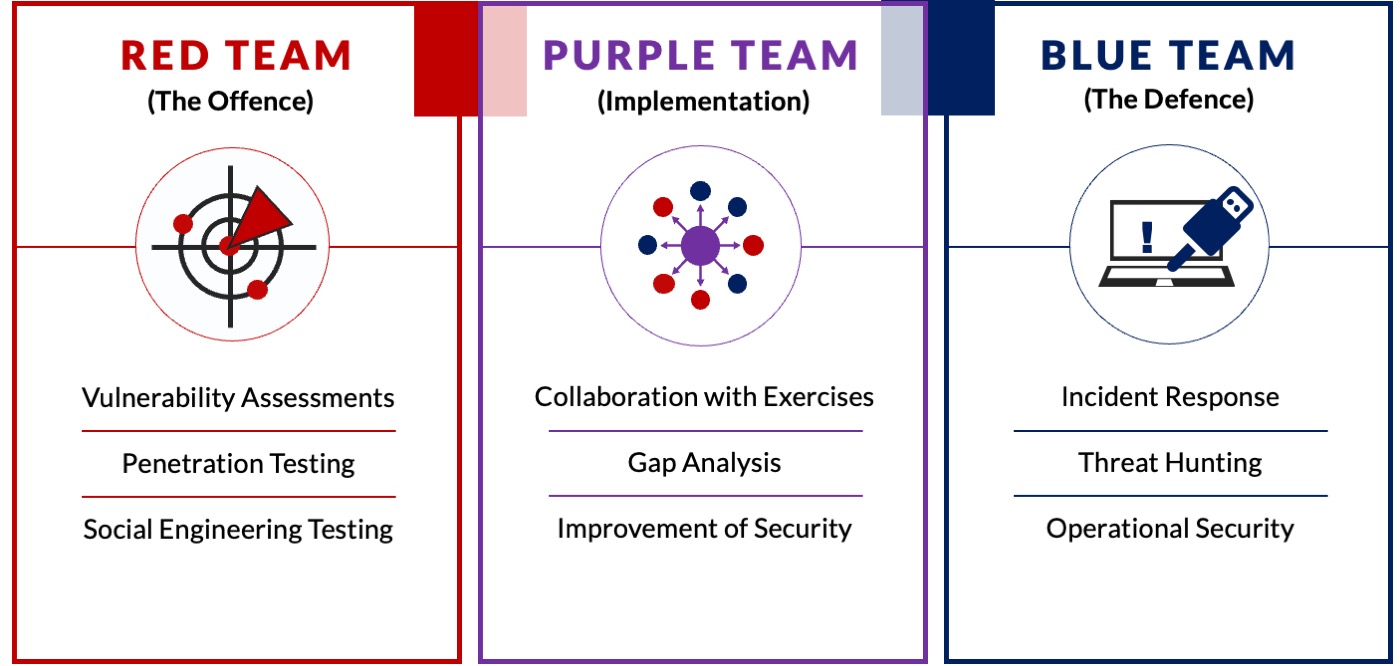
Relationship Between Cyber Security Pentesting and Red Team Activity
Complementary Roles in Cyber Security
Understanding the relationship between Cyber Security Pentesting and Red Team Activity is essential for organizations aiming to build a robust security framework. While they have their unique objectives and methodologies, both practices play complementary roles in bolstering an organization’s defenses.
- Pentesting as a Foundation:
- Targeted Defense: Pentesting focuses on identifying specific vulnerabilities in systems and applications. This systematic approach lays the groundwork for a stronger security posture.
- Proven Techniques: The results from pentesting offer valuable insights that inform relevant security measures and policies, creating a more fortified environment.
- Red Team as an Enhancer:
- Real-World Challenge: Red Team exercises assess the organization’s overall preparedness by simulating real-world attacks, challenging existing defenses more dynamically.
- Broad Coverage: By exploring wider avenues of attack—including human factors and physical security—Red Teams provide lessons that penetrate beyond technical vulnerabilities.
For instance, after a scheduled pentest uncovers weaknesses in an application, a Red Team could engage in further simulations to test the organization’s response and remediation efficacy under realistic threat conditions.
Collaboration for Enhanced Security Measures
The synergy between Cyber Security Pentesting and Red Team Activity can significantly enhance overall security measures, making it crucial for organizations to employ both strategies effectively.
- Integrated Strategy Development: When organizations combine insights from both pentesting and Red Team exercises, they can create a comprehensive security strategy. This strategy includes policies, procedures, and technological enhancements tailored to counter identified threats.
- Feedback Loop for Continuous Improvement:The insights gained from each practice feed into the other, establishing a feedback loop that drives continuous improvement. For example:
- Recommendations from pentests can inform the types of attacks a Red Team might simulate.
- Findings from Red Team challenges can spotlight areas where further pentesting would be beneficial.
A practical example could be a financial institution that initially conducts a pentest, revealing vulnerabilities in their online transaction system. Subsequently, a Red Team might mimic a complex phishing attack to test employee vigilance, leading to more informed training sessions. In conclusion, while Cyber Security Pentesting and Red Team Activity serve different purposes within the security landscape, their relationship is essential for building resilient defenses. By recognizing their complementary roles and fostering collaboration, organizations can implement enhanced security measures that not only identify weaknesses but also actively prepare for real-world threats, creating a comprehensive approach to cybersecurity.
This article is written by Fady Azzi
Fady Azzi is a Cyber Security expert, based in Sydney, Australia. Through quick and short videos full of interesting and trusted information, Fady’s channel aims to inform and educate people of all ages about cyber security, hacking, technology and many interesting topics.

0 Comments