IoT Security 101: Essential Tips for Protecting Your Devices
The Internet of Things (IoT) has rapidly evolved, connecting everything from household appliances to industrial machinery. However, with convenience comes vulnerability. The security of these devices is paramount in ensuring data integrity and user privacy.

Importance of Securing Your Devices
Securing IoT devices is not just a technical requirement; it’s essential for everyday life. Consider these points:
- Data Safety: Personal information can be compromised if devices lack security measures.
- Protection Against Cyber Threats: Inadequately secured devices can be exploited for cyber-attacks.
For example, a smart thermostat that isn’t secured could allow an intruder to track your daily routines or alter your heating, causing potential havoc. Thus, the urgency for robust IoT security measures is undeniable.
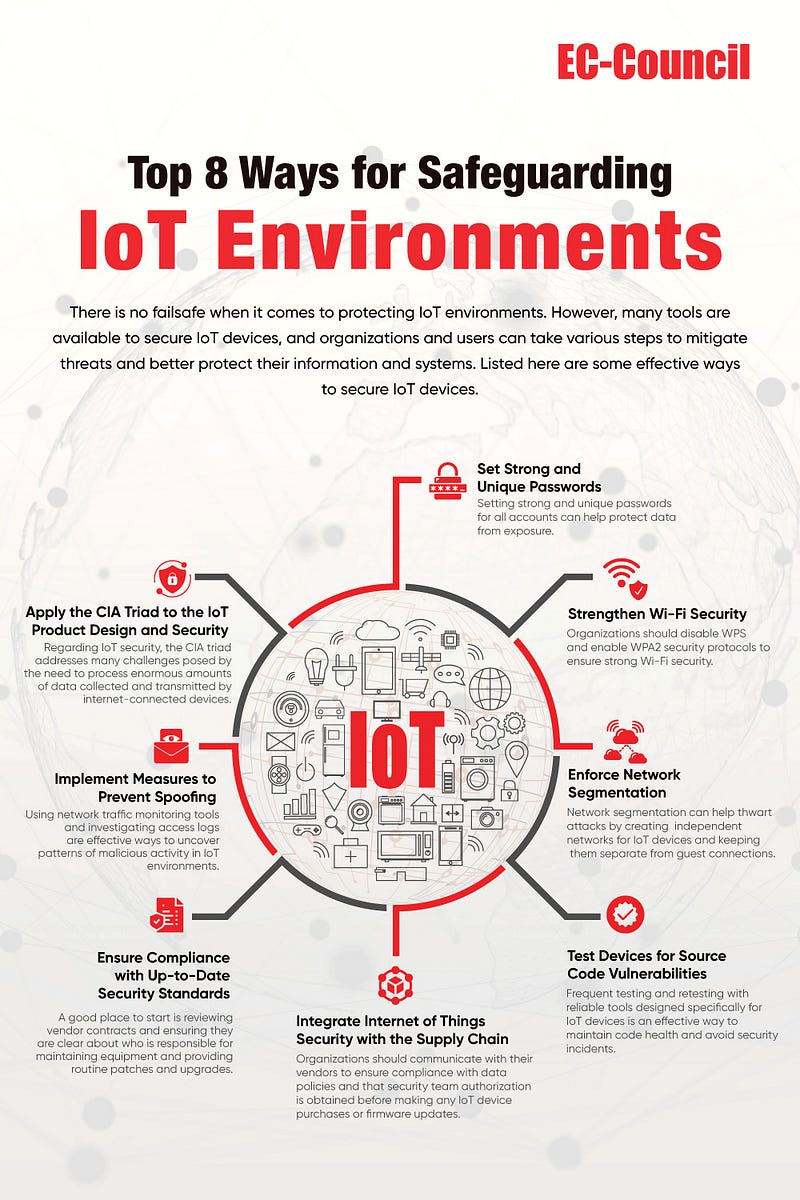
Common IoT Security Risks
Unauthorized Access
One of the most significant risks associated with IoT is unauthorized access. Many devices are designed with convenience in mind rather than security, making them easy targets.
- Default Passwords: Many devices come with factory-set passwords that users forget to change.
- Weak Security Protocols: Insufficient encryption can expose devices to remote hacking.
An anecdote to illustrate this is when a family was shocked to find their smart security camera had been accessed by a stranger, leading to a complete overhaul of their home security measures.
Data Breaches
Data breaches pose another substantial risk in the IoT landscape. As devices continually collect and transmit personal information, they become lucrative targets for cybercriminals.
- Sensitive Personal Data: This can include health information, location tracking, and financial details.
- Inadequate Data Protection: Many devices do not encrypt data effectively, making it susceptible to interception.
For instance, a healthcare IoT device that is attacked can lead to compromised patient records, impacting both privacy and the quality of care. It is crucial to be aware of these risks to fortify one’s security posture.
Essential IoT Security Tips
Keep Software Updated
To safeguard IoT devices, staying updated is crucial. Manufacturers regularly release software updates to patch vulnerabilities and improve security features.
- Automatic Updates: Enable automatic updates wherever possible to save time and effort.
- Manual Check: Regularly check for updates on less frequently used devices.
For example, a friend neglected to update his fitness tracker, ultimately exposing his data to hackers. When the update finally came, it fortified his device’s defenses!
Use Strong Passwords
Strong passwords are your first line of defense against unauthorized access. A unique, complex password can deter even the most determined cybercriminal.
- Length and Variety: Aim for at least 12 characters that include lowercase, uppercase, numbers, and symbols.
- Password Manager: Consider using a password manager to generate and store unique passwords for each device.
Remember the story of a family who fell victim to a home intrusion? It turned out that the intruder guessed the simple, default password of their smart doorbell. By prioritizing strong passwords, one can avoid becoming a statistic in the growing IoT security crisis.
Securing Your Home IoT Devices
Smart Home Security Cameras
Smart home security cameras provide invaluable peace of mind, but they also invite potential security threats.
- Change Default Settings: Always change the default username and password to something unique.
- Encrypt Video Streams: Ensure that your camera supports encrypted streaming for better security.
A neighbor once found their security footage accessed remotely due to lax settings, which prompted a neighborhood awareness campaign about upgrading digital security measures.
Smart Speakers and Virtual Assistants
Smart speakers and virtual assistants can streamline daily tasks, but they are always listening and collecting data.
- Mute Functionality: When not in use, physically mute your device to prevent it from picking up unintended conversations.
- Review Privacy Settings: Regularly check and adjust privacy settings to limit data sharing.
Consider how one user discovered that their smart assistant had recorded private conversations, leading to uncomfortable situations. Taking small steps can significantly enhance the security of these indispensable home devices, allowing users to enjoy their conveniences without the lurking threat of vulnerability.
Protecting IoT Devices in the Workplace
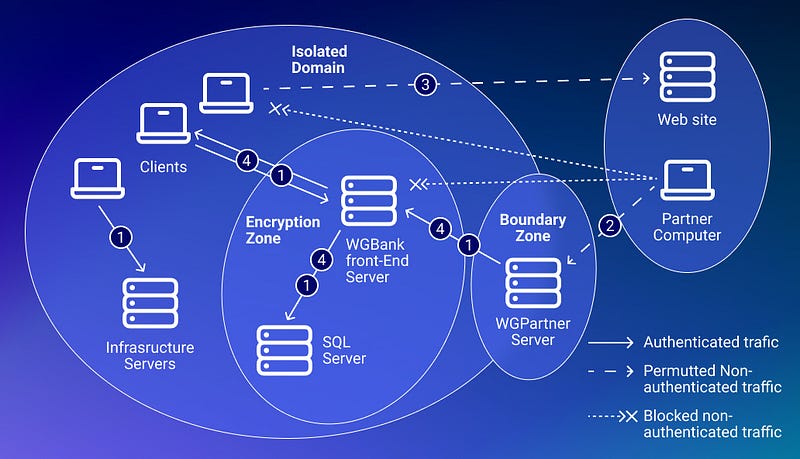
Secure Network Connections
In the workplace, a secure network is vital for protecting IoT devices from cyber threats.
- Use VPNs: Implement VPNs to encrypt data transmitted between devices.
- Firewall Protection: Enable firewalls to monitor and control incoming and outgoing network traffic.
A colleague experienced a data breach when a hacker accessed the company’s IoT devices through an unsecured Wi-Fi network. This incident served as a wake-up call to prioritize secure network practices.
Implementing Employee Training
Employee training is a crucial component of IoT security. Ensuring that staff understands potential risks can significantly reduce vulnerabilities.
- Regular Workshops: Conduct workshops to stay updated on IoT security best practices.
- Phishing Awareness: Teach employees to recognize phishing attempts that could lead to unauthorized access.
For instance, after an employee fell victim to a phishing scam related to IoT devices, the organization revamped its training program. By investing in proper training, businesses can empower their staff and create a culture of security awareness, minimizing the likelihood of future breaches.
IoT Security Best Practices for Businesses
Data Encryption
For businesses utilizing IoT devices, data encryption is non-negotiable. By encrypting data, organizations can protect sensitive information from unauthorized access.
- End-to-End Encryption: Implement end-to-end encryption for data in transit and at rest.
- Use Strong Algorithms: Select robust encryption algorithms to safeguard vital business information.
I recall a case where a mid-sized company avoided a potentially disastrous data breach simply because it had encrypted its customer data. This proactive measure rendered the data useless to would-be attackers, highlighting the importance of encryption in the ever-evolving landscape of cybersecurity.
Regular Security Audits
Conducting regular security audits is another pivotal best practice for ensuring IoT security.
- Assessment of Vulnerabilities: Regularly identify and assess vulnerabilities within the network and devices.
- Policy Updates: Update security policies based on audit findings to address new threats.
When a tech firm implemented quarterly security audits, they uncovered outdated firmware on several devices, which had left them vulnerable. Following the audit, they prioritized updating their systems, solidifying their defenses and ensuring ongoing protection against rising security threats. By embracing these best practices, businesses can fortify their IoT security posture effectively.
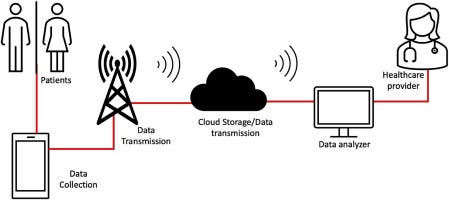
Securing IoT in Healthcare
HIPAA Compliance
In the healthcare sector, ensuring the security of IoT devices is critical, especially under the Health Insurance Portability and Accountability Act (HIPAA).
- Protected Health Information (PHI): Any device collecting or transmitting PHI must adhere to HIPAA regulations.
- Regular Risk Assessments: Conduct risk assessments to evaluate existing security measures and identify vulnerabilities.
A friend who works in a hospital recounted how they faced significant fines for non-compliance regarding IoT devices, which led to a comprehensive review of all their data handling processes. By prioritizing HIPAA compliance, healthcare providers can protect patient privacy while leveraging the benefits of IoT technology.
Biometric Authentication
Biometric authentication offers a robust security solution for healthcare IoT devices.
- Unique Identifiers: Utilizing fingerprints, facial recognition, or iris scans strengthens access controls.
- Patient Safety: Biometric systems can ensure that sensitive patient data is only accessible to authorized personnel.
For instance, a healthcare facility implemented biometric access for its electronic health records. This not only enhanced security but also streamlined healthcare providers’ access to vital patient information. As IoT continues to reshape healthcare, biometrics serves as a vital tool in securing patient data while maintaining compliance with industry regulations.
Ensuring IoT Security in Industrial Settings
Critical Infrastructure Protection
In industrial settings, protecting critical infrastructure is paramount. IoT devices often monitor and control essential systems, making them attractive targets for cyberattacks.
- Segmentation: Implement network segmentation to isolate critical infrastructure from less secure networks.
- Redundancy Measures: Build redundancy into essential systems to minimize downtime in case of a breach.
A colleague shared a harrowing experience of a manufacturing facility that faced a ransomware attack targeting production lines due to unprotected IoT devices. This incident sparked a complete overhaul of their security strategy.
IoT Device Monitoring
Constant monitoring of IoT devices is essential to detect anomalies and potential intrusions.
- Real-Time Alerts: Utilize solutions that provide real-time alerts for suspicious activities or unauthorized access attempts.
- Data Analytics: Employ data analytics to establish normal operational patterns and identify deviations efficiently.
For example, a utility company implemented a monitoring system that flagged unusual data traffic from its smart meters. This early detection allowed them to thwart a potential security breach and reassess their IoT security protocols. In industrial environments, proactive IoT security measures are not just beneficial; they’re essential for ensuring the safety of operations and data integrity.
Securing IoT Devices in Transportation
Connected Vehicles
The integration of IoT in connected vehicles has transformed transportation, but this also presents unique security challenges.
- Software Updates: Regularly update vehicle software to patch identified vulnerabilities.
- Secure Communication Channels: Implement encryption for communications between connected vehicles and external networks to prevent unauthorized access.
A friend who works in automotive IT recalls a concerning incident where a hacker remotely accessed a connected car, altering its settings while its owner was driving. This event highlighted the critical need for reinforced security measures in connected vehicles.
GPS Tracking Devices
GPS tracking devices are invaluable for fleet management and personal transportation, yet they are vulnerable to hacking and spoofing.
- Data Encryption: Ensure that the data transmitted from GPS devices is encrypted to protect against interception.
- Access Controls: Limit access to tracking data only to authorized personnel to reduce the risk of misuse.
For instance, one logistics company faced significant downtime when hackers spoofed their GPS signals, causing misrouted shipments. After this event, they prioritized enhancing the security of their GPS tracking solutions, emphasizing the importance of robust protective measures in the transportation sector. With the rising reliance on IoT devices, securing these systems has never been more crucial.

IoT Security Regulations and Compliance
GDPR
The General Data Protection Regulation (GDPR) sets a high standard for data protection and privacy in the European Union, impacting IoT devices significantly.
- Consent Requirement: Businesses must obtain explicit consent from users before collecting personal data through IoT devices.
- Data Rights: Users have rights to access, rectify, and erase their personal data, which extends to data collected by IoT solutions.
A colleague in a European tech firm remarked on the challenges they faced when adapting their IoT services to comply with GDPR, but ultimately, it strengthened their commitment to safeguarding user privacy.
California IoT Security Law
Enacted in 2020, California’s IoT Security Law mandates basic security requirements for manufacturers of connected devices.
- Default Passwords: Manufacturers must ensure that devices come with secure default passwords that are unique and not easily guessed.
- Security Updates: The law encourages ongoing security updates for connected devices to address newly discovered vulnerabilities.
For example, a company that manufactures smart home devices had to revise its product development strategies to align with this new law. After implementing these changes, they found increased consumer trust and satisfaction. As regulations continue to evolve, compliance becomes not just a legal obligation but a pivotal factor in establishing credibility in the market.

Future Trends in IoT Security
AI-Powered Security Solutions
As IoT continues to evolve, one of the most promising trends is the integration of AI-powered security solutions.
- Anomaly Detection: AI can analyze vast amounts of data to identify unusual patterns that may signify a security breach.
- Automated Response: With advanced algorithms, AI can automate threat responses, enabling faster action against potential attacks.
I recall a case where a smart home system employed AI to detect and thwart a security threat in real-time, showcasing the potential of AI in enhancing IoT security.
Blockchain Technology for IoT Security
Another groundbreaking development in IoT security is the adoption of blockchain technology.
- Decentralization: Blockchain provides a decentralized way of securing data, reducing the risk of centralized vulnerabilities.
- Immutability: Transactions recorded on a blockchain are immutable, ensuring that data integrity is maintained throughout.
For example, companies exploring blockchain for supply chain IoT devices found that it not only strengthened security but also increased transparency. As we look to the future, embracing these innovative technologies will be crucial in addressing the security challenges associated with the expanding IoT landscape.
This article is written by Fady Azzi
Fady Azzi is a Cyber Security expert, based in Sydney, Australia. Through quick and short videos full of interesting and trusted information, Fady’s channel aims to inform and educate people of all ages about cyber security, hacking, technology and many interesting topics.

0 Comments