Unveiling the Secrets: The Art of Steganography in Image, video and audio Files
What is Steganography?
Steganography is the art and science of hiding information in plain sight. Unlike encryption, which scrambles the content of a message to make it unreadable without a key, steganography conceals the very existence of the message. It allows senders to embed secret information within innocuous files, such as images, audio, or video files, ensuring that unwitting observers remain oblivious to the hidden data. This subtlety makes steganography a powerful tool in the realm of cybersecurity. For example, think of a digital image, like a family photo. Within the pixel data, additional messages can be embedded, allowing the sender to communicate discreetly.
History of Steganography
The history of steganography is as rich as it is fascinating. It dates back to ancient times, with notable instances including:
- Ancient Greece: Histiaeus, a ruler, tattooed a message on a slave’s shaved head, waiting for the hair to grow back before sending him to deliver it.
- World War II: Both sides used steganography through microdots — tiny images containing hidden information secured inside other documents.
Over the centuries, the methods have evolved from physical carving and ink to digital embedding, showcasing steganography’s resilience and adaptation in the face of technological advancement. Today, it stands as a crucial technique in securing communications and protecting sensitive information from prying eyes.

Steganography in Image Files
Techniques Used in Image Steganography
Image steganography employs several sophisticated techniques to hide information within image files effectively. Some popular methods include:
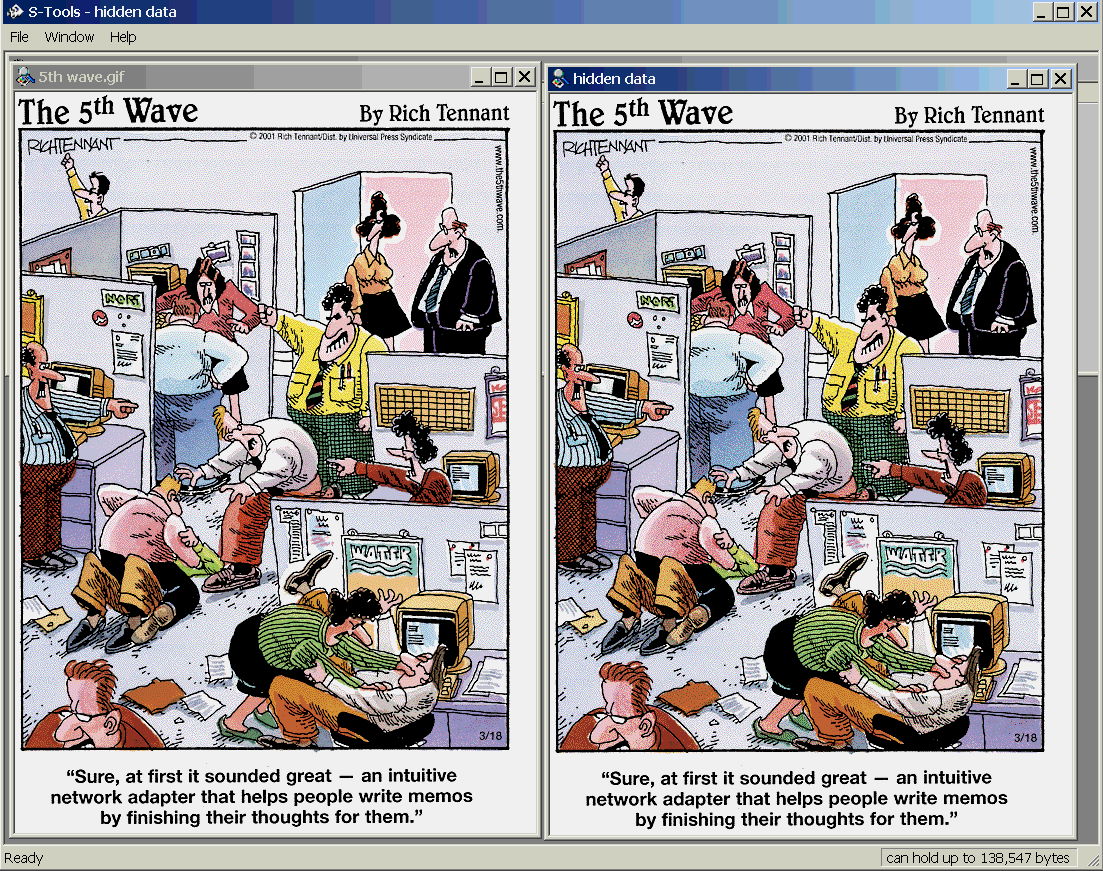
- Least Significant Bit (LSB): This technique alters the least significant bits of pixel values to encode information. For instance, changing a pixel’s value from 11001010 to 11001011 can hide one bit of data without impacting the overall image significantly.
- Masking and Filtering: Used primarily in bitmap images, this technique involves altering specific areas of an image to embed information, akin to a digital watermark.
- Transform Domain Techniques: These include methods like Discrete Cosine Transform (DCT) that embed messages into the frequency domain of images, providing robustness against common image manipulations.
Each of these methods allows for varying degrees of security and invisibility, catering to specific needs in digital communication.
Tools for Image Steganography
In the realm of image steganography, several user-friendly tools help embed and extract hidden messages efficiently. Noteworthy options include:
- Steghide: A powerful tool that supports various formats like JPEG and BMP, allowing users to hide messages and compress them for additional security.
- OpenStego: An open-source software that provides watermarking and data hiding features, making it accessible for all skill levels.
- SilentEye: A graphical interface tool that lets users visually embed information into images, offering both novice and experienced users an easy handling experience.
These tools demonstrate the dynamic nature of steganography, allowing users to safeguard their communications in an increasingly digital world. Each tool caters to specific use cases, making it easier to choose the right one based on individual needs.

Steganography in Video Files
Embedding Data in Video Files
Steganography within video files takes the art of information concealment to a more dynamic level. This method allows large amounts of data to be hidden within the frames of a video, offering an appealing combination of capacity and complexity. Techniques utilized for embedding data include:
- LSB (Least Significant Bit) Method: Just like in image files, the least significant bits of pixel values in video frames can be altered for data embedding.
- Temporal Domain Techniques: These methods utilize the differences in successive frames, enabling the encoding of messages across multiple frames, often unnoticed during playback.
- DCT-based methods: By manipulating the frequency coefficients of transformed video data, data can be subtly embedded while maintaining visual quality.
For example, imagine a promotional video with embedded URLs directing viewers to further documentation.
Detecting Steganography in Videos
Detecting steganography in videos presents unique challenges due to the nature of the medium. As sophisticated as steganography techniques are, so too are detection methods. Here are a few effective techniques used:
- Statistical Analysis: This involves analyzing video frames for anomalous patterns, such as irregular changes in pixel values, which can indicate hidden information.
- Visual Inspection: Practitioners may look for noticeable artifacts or distortions that deviate from normal video data patterns, signaling the presence of hidden messages.
- Watermarking Detection: When a steganographic method uses watermarking, tools can be employed to identify these marks, indirectly revealing hidden data.
As with any technological advancement, the duel between steganography and detection continues to evolve, with each side pushing the boundaries of creativity and sophistication. Understanding these methods aids cybersecurity professionals in both implementing secure communications and identifying potential breaches.
Steganography in Audio Files
Hiding Messages in Audio Files
When it comes to audio files, steganography employs clever techniques to embed hidden messages directly into sound recordings. This technique can be particularly effective given that many audio formats offer ample data capacity without significant quality loss. Techniques include:
- Least Significant Bit (LSB) coding: Just like in images and video, LSB can be applied to audio files, modifying the least significant bits of audio sample values to encode secret information.
- Phase coding: This involves altering the phase of a sound wave to obscure messages in ways that are inaudible to the human ear.
- Spread Spectrum: By distributing data across a wide frequency range, this method makes it harder for unauthorized individuals to detect embedded messages.
For example, a simple music track could have a covert message embedded within its audio stream, undetectable to the average listener but accessible to the intended recipient.
Audio Steganography Tools
A variety of tools exist for audio steganography, enabling users to efficiently hide and retrieve messages within audio files. Notable tools include:
- Audacity: This open-source audio editor can be equipped with plugins for audio steganography, allowing custom implementations.
- Sonic Visualiser: A tool specializing in visualizing audio data, it can assist in identifying hidden messages through its analytical features.
- StegHide: Similarly to its image counterpart, it allows users to hide information within various audio formats while maintaining quality.
These tools exemplify how audio steganography is becoming more accessible, making it an increasingly attractive solution for secure communications in the digital landscape. By understanding these practices and resources, cybersecurity professionals can better protect sensitive information shared through audio channels.

Comparison of Steganography Techniques
Image vs. Video Steganography
When comparing image and video steganography, several key differences emerge.
- Capacity: Video files generally have a much higher data capacity than images. A standard video can hide significantly more information due to its extended duration and complexity.
- Complexity: Video steganography tends to be more intricate as it involves analyzing multiple frames and maintaining a consistent quality across the timeline. In contrast, image steganography is typically simpler, often executed through techniques like LSB.
- Detection:Steganalysis is generally more challenging in video files due to the dynamic content, which can make the hidden data less detectable compared to static images.
For instance, while a single JPEG may hide a few bytes, a video file can obscure several kilobytes, making it suitable for larger data requirements.
Audio vs. Image Steganography
The comparison between audio and image steganography reveals distinct advantages and challenges for each medium:
- Human Perception: Audio steganography often uses techniques that leverage the limits of human hearing, allowing for data embedding in ways that go unnoticed. In contrast, changes in images can be more visible, potentially revealing the presence of hidden messages.
- Data Volume: Image files can usually store larger amounts of data compared to audio, given the nature of visual pixels versus audio sample data.
- Manipulation: Audio files are susceptible to quality degradation when manipulated, which can affect hidden data. Images, generally more forgiving to alterations, can retain their integrity better post-manipulation.
Engaging in these comparisons helps cybersecurity teams understand the optimal contexts for each steganography technique, enhancing their ability to deploy secure communication strategies effectively tailored to the type of media being used.
This article is written by Fady Azzi
Fady Azzi is a Cyber Security expert, based in Sydney, Australia. Through quick and short videos full of interesting and trusted information, Fady’s channel aims to inform and educate people of all ages about cyber security, hacking, technology and many interesting topics.

0 Comments